How Cupcake Actually Works: A Technical Deep(ish) Dive
Cupcake turns any old phone into a powerful hardware wallet, but how does it actually work under the hood? We're breaking down the security model, from secure enclaves and offline key storage to animated QR transactions.

If you’ve been keeping an eye on Cake Wallet lately, you’ve most certainly heard of our latest app, Cupcake. But were you left wondering exactly how it works, how it ensures your funds are secure, and how it compares to a traditional hardware wallet? We’ll break all of that down in this (slightly) deeper dive, as while we build in the open (FOSS FTW!) it can be hard to get a grasp of how things work technically for those who aren’t deep in the code.
What is Cupcake?
In case you missed it, Cupcake is the latest app in the Cake Wallet family, focused on making crypto security possible for everyone. No more waiting weeks for shipping and customs, no more $200+ costs, no more terrifying data breaches. If you have an old phone lying around, Cupcake lets you turn it into a powerful hardware wallet with just a few taps. But how does all of this actually work under the hood? Is it actually secure?
Why do we need hardware wallets, anyways?
Private key security is the most critical aspect of security in crypto, and the core reason people like you want to use a hardware wallet to secure their funds. While mobile phones and hot wallets have come a long way over the years, some users prefer not to use an app that’s always-online for storing their wealth. Are hot wallets fine for spending money and NFTs? Sure, but we can do better when it comes to securing generational wealth.
Enter hardware wallets — specialized hardware devices built exclusively to store your private keys and sign transactions. While they’re often hideous and hard to use, they allow you to keep your private keys offline and entirely distinct from your digital life, and yet you can connect them to a software wallet like Cake Wallet to easily view your balance and see transaction history even when you’re apart from your hardware wallet. They’re a fantastic tool and have set the standard for security over the last decade, but they also come with many downsides that we’ve already covered at length in our last blog post on Cupcake.
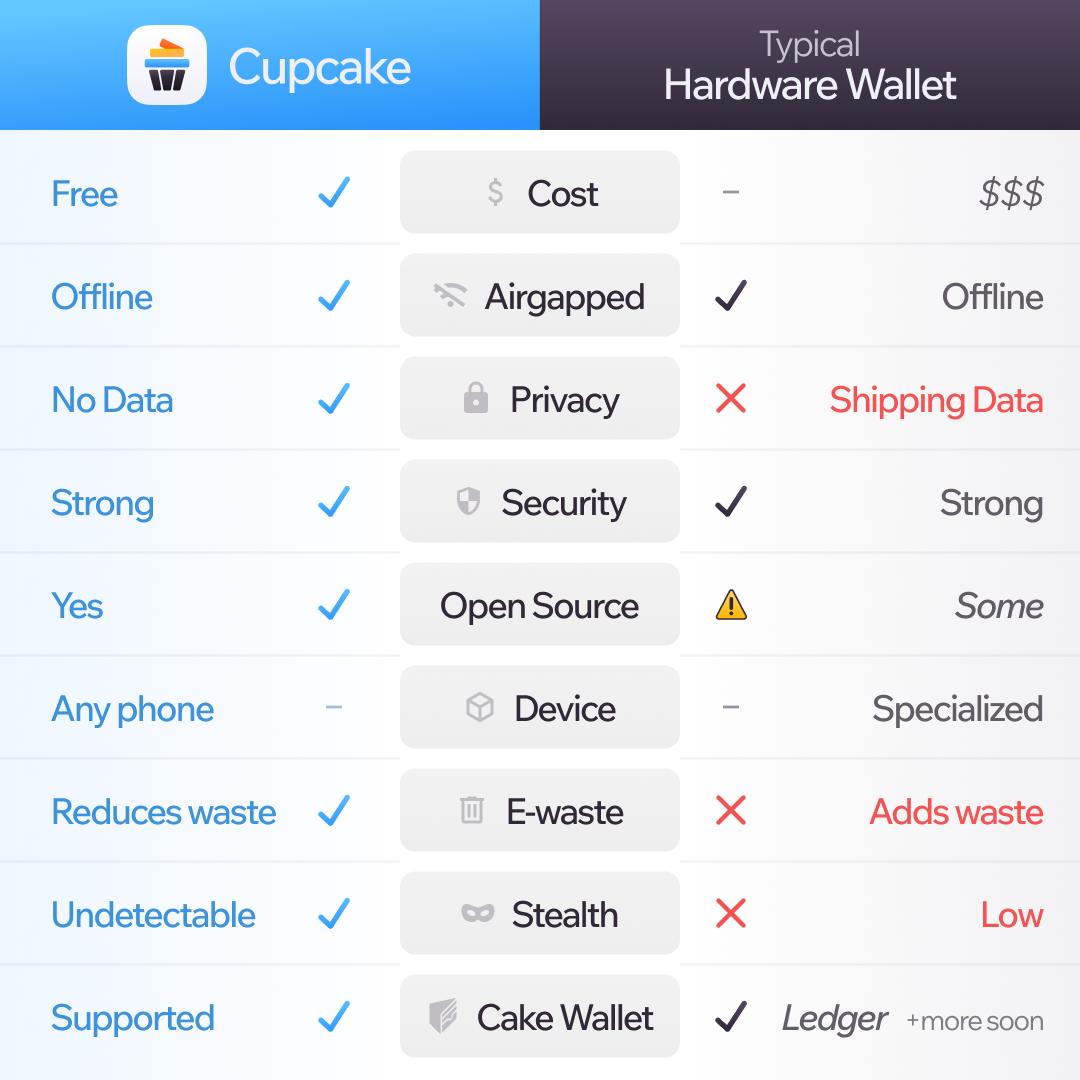
While many current crypto users may already have a hardware wallet, we think we can bring 90% of the security they offer to the other 99% of the world. Cupcake lets us build a user-friendly, approachable, and 100% free and open source alternative to hardware wallets, because we think the 99% deserve better.
Cupcake’s security model

- Security at rest
To ensure that Cupcake users get the best possible security for their private keys, Cupcake utilizes the best local security the phone being used can offer. For highly secure devices like Google Pixels and iPhones, that means storing secrets in a secure enclave to ensure that no other apps on the device can access them. Android and iOS both enforce strict app isolation to prevent malicious apps installed on a device from accessing secrets and data from other, legitimate apps, and all of that protection is employed with Cupcake as well.
We also leverage the secure enclave on those devices to enforce PIN brute-force protection, ensuring that an attacker with access to your unlocked phone can’t easily get into Cupcake and access keys or sign transactions. Breaking this PIN protection would require breaking your phone’s security model, something that is extraordinarily difficult on an up to date, modern device.
Lastly, the wallet file itself has an encryption key that is derived from both your own unique PIN or password for Cupcake as well as a part generated on your phone’s secure enclave. This means that even if your phone was confiscated and all of the storage was captured, the wallet files will still have an effective layer of protection.
For those using very old devices or ones without a secure enclave (a rarity these days), we’ve implemented a novel use of proof-of-work to prevent PIN brute-forcing as best we can. When we detect that there is no secure enclave on the device, we still enforce a multi-layered secure storage approach at-rest while forcing the phone to do intensive calculations that increase in difficulty with each failed PIN attempt. While this isn’t as strong of protections as those enforced by a top-tier secure enclave, it will still prevent the most common types of attacks — evil maid attacks and attacks of opportunity.
- Security in flight
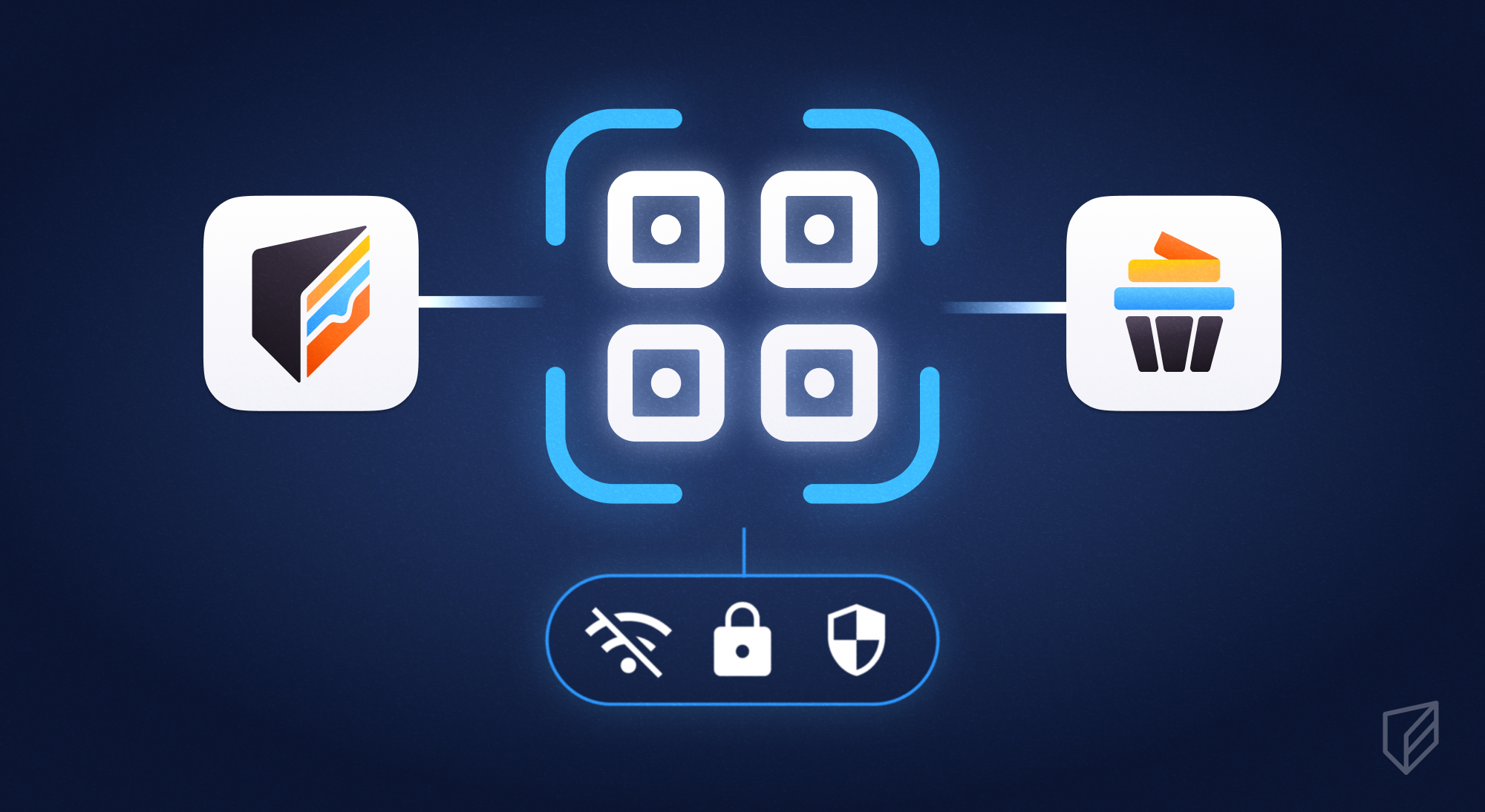
We’ve entirely disabled network permissions for the Cupcake app on both Android and iOS, ensuring that the operating system will never allow Cupcake itself to connect to the internet. But if your keys are so secure and Cupcake can’t go online, how do you actually sign transactions? We’ve gone with the industry standard approach to signing transactions without ever bringing your keys online, relying on animated QRs to transmit data between your Cupcake device and your device running Cake Wallet.
When you want to make a transaction, you initiate it on Cake Wallet just like any other transaction. Enter the address, amount, etc., but what normally would be a send button on Cake Wallet actually opens up a new screen with an animated QR code. This QR code contains the unsigned transaction, with all of the details needed for Cupcake to validate the transaction, display all of the details for you on your Cupcake device, and then sign when ready. Then, Cupcake shows its own animated QR code that contains only the signed transaction, with no private keys ever being shared.
Scan that QR code with Cake Wallet, hit send, and you’ve just made a transaction while keeping your private keys 100% offline the entire time. It’s pretty magical, if we’re honest.
- Security when updating

One of the most common questions we’ve gotten about Cupcake since launching it is “how can I update Cupcake without being online?” For most users, the best approach is to allow their Cupcake device to come online for app and OS updates, as the most common risks would be that the device itself would have a vulnerability that allowed a PIN bypass or an exploit for an attacker with possession of the device. This relies on Cupcake’s lack of network permissions to ensure that keys stay offline, while still allowing for easy updates to Cupcake and the phone’s OS.
For the more paranoid among us (you know who you are), an alternative option would be to keep the device you want to use Cupcake on always offline and simply install updates by transferring the latest APK file with a flash drive or similar. Unfortunately due to Apple’s blocking of side-loading in most geographies this will usually only work on Android, but is a good approach for those with an old Android phone lying around. This approach may also be more reasonable for those devices that are already past their lifecycle of security updates and wouldn’t get OS updates anymore regardless.
In general, Cupcake also relies on OS security to ensure that even if you were tricked into installing a malicious version of Cupcake from an outside source, there is no way to install it over top of the legitimate app. We take app signing security very seriously, and that security acts as a guarantee that you can only install official app updates that are properly signed by our teams app signing keys.
Cupcake best practices
If that was way too much to read, here are a few rapid-fire best practices to ensure you get the best security when using Cupcake:
- Use a Google Pixel or Apple iPhone for the strongest secure enclave security
- Use a device that still receives security updates
- (Recommended) Use a hardened operating system like GrapheneOS for even more security
- Use a strong, securely generated device PIN or password, preferably six digits or more
- (Recommended) Whenever possible, use a strong password instead of a PIN for better security
- Use a strong, securely generated password for Cupcake
- Keep your device offline unless actively updating the OS or Cupcake itself
- (Recommended) Perform OS and Cupcake app updates offline when using an Android device
But wait, why do we support hardware wallets in Cake Wallet then?
While Cupcake solves a lot of needs for those in the Global South and those at high risk (i.e. journalists, dissidents, and activists), many crypto-native users still love the set of tradeoffs that traditional hardware wallets bring. A good hardware wallet like the Ledger Flex, Foundation Passport, or Trezor Safe 5 brings a smaller attack surface, a familiar UI, and broader multi-crypto support (for now). Not only that, as they are devices that are incapable of network connections entirely, keeping them offline has less tradeoffs and hassle. Lastly, as Cupcake’s security depends heavily on what phone you choose to run it on, reasoning with the security model of a specialized hardware wallet is much simpler overall.
When you combine the 90% of security that Cupcake brings to the 99% of people in the world along with the maximal security that existing hardware wallets bring to the 1% of crypto-native users in one powerful app (that’s Cake Wallet!) you have the best of both worlds. Your crypto, your hardware, your choice. We are proud to also embrace hardware wallets!
Conclusion
The goal of Cupcake is to bring 90% of the security of hardware wallets to the 99% of people in the world who don’t have a hardware wallet and often have no access to one. We believe we’ve made huge strides to accomplish that goal, with security being top-of-mind when designing and improving Cupcake. We’re excited to bring even more advanced functionality to Cupcake over the coming months, with things like Litecoin MWEB, Silent Payments, BIP 353 DNSSEC verification and more on the roadmap.
Have something else you’d like to see in Cupcake, or have a further question about the security model? Don’t hesitate to drop us a line or reach out to our incredible support staff!
